- Choice of forest/root domain names
- Number, type, location, and sizing of domain controllers
- Special administrative issues that may require multiple domains/forests
- Administration model/OU structure
- Planning sites/subnets/replication
Like Windows Server 2008 and Windows Server 2008 R2, installation is a two step process:
- Install the Active Directory Domain Services (ADDS) Role
- Promote the first DC in the forest
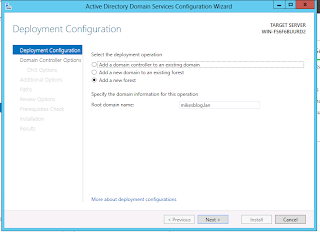
Next determine the domain and forest functional level for the new Active Directory Forest/Domain. A rule of thumb is to not choose a level that is greater than the oldest OS version expected to be used for the domain controller (i.e. don;t pick 2008 or 2008 R2 if you plan to promote a 2003 domain controller). Note that this setting has no implications for the types of clients/non DC servers that can be joined to the domain. This step also allows you to decide whether to install the DNS role and create AD-integrated zones for the new forest/domain. Most native Windows environments will need at least 1 DNS server (and preferably more to not create a single point of failure). The first DC promoted in the forest has to be a global catalog server and cannot be a read-only domain controller (RODC). Finally, the directory services restore mode password should be documented in the event that the directory needs to be restored from backup.
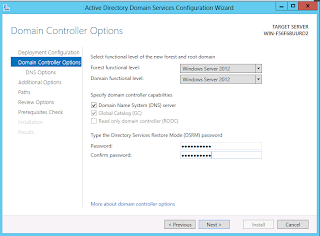
If you choose to install the DNS role, you may have the option to create a delegation for the server to host the piece of the DNS namespace that is covered by the forest/domain. Most companies that invent a top-level domain will not have the ability to do this. Organizations that use a subdomain of their existing DNS namespace or use a real registered domain may have the ability to create the delegation.
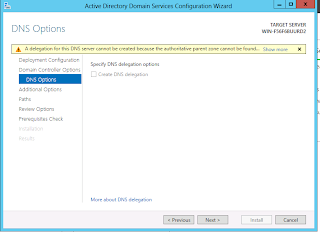
Next, choose a NetBIOS domain name to correspond with the new forest/domain. This is a single label that is typically the first component of the domain name (ex ad.microsoft.com -> AD, mikesblog.lan -> MIKESBLOG).
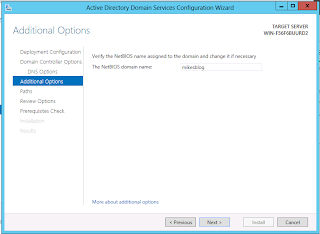
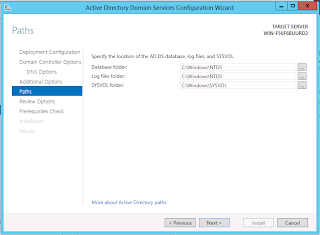
Finally, configure the storage location for the Active Directory database and transaction logs. For domains expecting heavy DC use, it may be advantageous to place the database and log files on separate high speed volumes. The SYSVOL folder should be placed in a location with adequate space to store group policies, logon scripts, and anything else that the domain admins want to replicate to all of the DCs. This may need to be moved to external storage if the organization heavily utilizes group policy software installation.
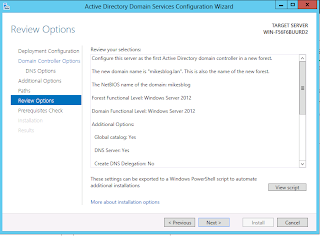
Finally, you can review the options and generate a script for deploying DCs with the same configuration.
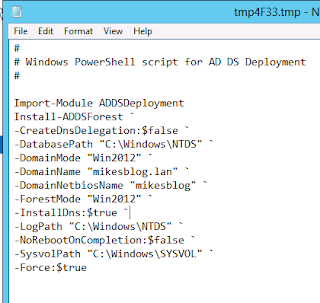
Below is an example of the script generated to create a new forest using the Install-ADDSForest cmdlet.
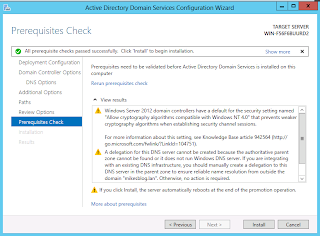
After that, your new domain is set up, but the domain controller that you just created is a single point of failure. You should probably install a second one.
No comments:
Post a Comment